Developers and software-as-a-service (SaaS) providers can develop cloud services, that can be integrated with Azure Active Directory to provide secure sign-in and authorization for their services. To integrate an application or service with Azure AD, a developer must first register the application with Azure Active Directory with Client ID and Client Secret. Creating a service principal, try using Azure Active Directory Managed Service Identity for your application identity.
Any application that wants to use the capabilities of Azure Active Directory must be registered in an Azure. The app registration will give the Client ID which is App ID and Client Secret, Sign-On URL.
How to Create Client Id and Client Secret for Azure
1) Log in to the Azure portal.
You must have sufficient permissions to register an application with your Azure Active Directory tenant and assign the application to a role in your Azure subscription.
2) On the top search bar, type “Azure Active Directory” and click the Active directory or Click on More Services on the left-hand side, and choose the Azure Active Directory.
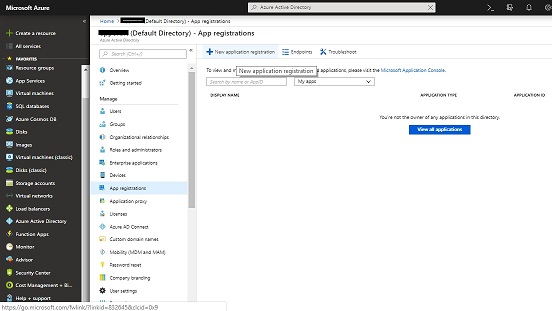
3) Click on App registrations and Click “New application registration”
- Make sure App registration is allowed for the user account through the Azure Active Directory -> select User settings and “App registrations” selected as “Yes“
4) Provide a name and URL for the application.
- Select Web app / API for the type of application and Click Create.
You have created your application.
How to Get application ID and authentication key
To get the application Client Id and Key details.
1) From the App registrations in Azure Active Directory, select your application.
2) Copy the Application ID
3) Click Settings on the same window.
4) To generate an authentication key, Click Keys.
azure-app-registration-step4
5) Update a description of the key, and a duration and value which is your password, select Save.
Now the Client ID and Client Secret will be used for your configurations or any other rest clients.
How to Get Azure tenant ID
It is required to pass the tenant ID with your authentication request.
1) Select the Azure Active Directory.
2) To get the Azure tenant ID, select Properties for your Azure AD tenant.
How to Assign Role to application
To access the subscription, you must assign the application to a role. Decide which role represents the right permissions for the application.
1) Select your Subscriptions (On the top search bar, type “Subscriptions“).
2) Click Access Control (IAM)
3) Select Add
4) Select the role you wish to assign to the application.
5) Select Save to finish assigning the role. You see your application in the list of users assigned to a role for that scope.
How to create an Azure Client ID and Client Secret using AZ command line
1) Login with Azure account.
- It will ask you the confirmation and update an auth configuration to local. Make sure you are having a valid subscription.
# az login
1) Create Service Principle
- You will get the tenant id, appid and auth password.
# az ad sp create-for-rbac --name <app_name> --password <passwd>
{
"appId": "8334373-0dd9-438c-b563-2a6dbd8248c9",
"displayName": "my-test",
"name": "http://my-test",
"password": "password",
"tenant": "9a562b46-a92e-2113-4r33-7ca4c3598479"
}
2) Assign Role
# az role assignment list --assignee <app_id>
[
{
"id": "/subscriptions/<su_id>/providers/Microsoft.Authorization/roleAssignments/efccd2ae-236o-41de-ba22-58d2e6146164",
"name": "efccd2ae-4e20-41de-b022-58d2e6046164",
"properties": {
"principalId": "367a4295-5oo5-4162-ae71-248534k463a2",
"principalName": "http://my-test",
"roleDefinitionId": "/subscriptions/<su_id>/providers/Microsoft.Authorization/roleDefinitions/b24988ac-6180-42a0-ab88-20f7382dd24c",
"roleDefinitionName": "Contributor",
"scope": "/subscriptions/<su_id>"
},
"type": "Microsoft.Authorization/roleAssignments"
}
]